"All warfare is based on deception." - Sun Tzu
Computer virus - in hacker slang as 'virii', an incorrect and satiric spelling. In Latin, 'virus' stands for 'poison, venom, toxic & pungency. In a more professional explanation, computer virus is:
- A self-replicating program.
- Rouge program/script that performs malicious task(s).
- An ingenious creation and first evidence of Artificial intelligence.
After 8 months of hardworking, our research is nearly complete. Research and development of next generations of computer virus. We are able to create 3 variants of powerful computer virus that can do every programmed task while seek & analyze new tasks, all by themselves. We also come up with totally new techniques of both offensive and defensive sides.
Here are the 2 'harmless' variants that we want to make public (They don't spread crazily but they can still cause some catastrophic + side effect. NONE of the Antivirus can detect them so be careful; If you are a researcher, feel free to modify or play with it. If you are a criminal, then fuck you!). The 3rd variant is under development. We are going to release our source codes soon in near future.
Offensive:
- Able to terminate and remove Antivirus or detection system completely.
- Replication with an impressive speed.
- Nuke - our new technique for self-destruction, once compromised. Which means it can do such things as wipe clean data or damage firmware.
- Self-mutation to cope with the infected system.
- Reside in RAM.
- Infect firmware of hardware.
Defensive:
- Disguising as any file in the Win32 systems.
- Self-crypt - generate multi-layers of encryption. Featuring our encryption, BlackCode.
- File binding.
- Anti-sandbox & emulation.
- Meltdown - This is a cutting edge for our virus development of armouring technique
- Withstand hard-drive wipe - time to buy yourself a new PC. (This isn't new but our version is much improvised)
I am no genius. Neither my colleagues. We are just a bunch of hobbyists who want to experience with challenges. When come to writing virus, I always ask questions that normal people might think I'm a psychopath! Can I damage this? Can I infect this? How could I wreak this/that without getting detected? How can I nuke a system under a few minutes?
Anyways, here are a list of team members who had or has involved in this behemoth project:
Mentor - Project manager & Researcher.
Waffles (me) - 2nd project manager, core & AI programmer.
Computer112 - Concept programmer & cryptographer. (He is no longer part of the project. Creator of BlackCode encryption)
silencefreedom - Core programmer & Researcher
NorskeDrittsekk - Core programmer
ZionJD - Cryptographer
NorskeDragon - Core programmer
binbashLinuxAhole - Core programmer
Traz - AI programmer
MindFreaker - AI programmer
Cr22ck - Core programmer
DeathWaltz - Core programmer
Trev0r - Adviser
T1g33r - Adviser
Pic below is showing a core section, let's say part of the brain of the BlackRain computer virus.
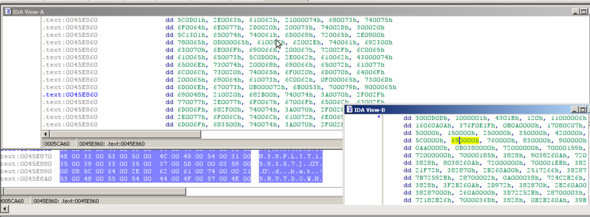
VicariousE
Makes me wish I never threw away my old motherboard, that would interleave the reformatting.... ah, I see, infecting the BIOS itself. That's been happening with routers for a while now....
Anyway, saw this on a Russian site and thought of you, since you've come out of the woodwork again :3 <a href="http://rt.com/usa/news/texas-1000-us-government-906/">http://rt.com/usa/news/texas-1000-us-governmen t-906/</a>
Wurfel-Waffles
OMG, I was amazed at what Texas University did when I read the BBC (I like to read Russia Today too, seem to be the only 'real news' nowadays).
I am 99% certainly sure Iran used the same technique to brought down CIA drone http://rt.com/usa/news/iran-drone -hack-stealth-943/
Infecting BIOS is probably the oldest and most effective technique for hiding malware, ever.